Security Operations Centers (SOCs) stand as the frontline defense against evolving cyber threats, requiring robust measures to safeguard critical assets and sensitive data. Implementing CIS (Centre for Internet Security) Hardening plays a pivotal role in fortifying SOC environments and ensuring their effectiveness in combating modern-day cyber risks. Understanding SOC and Its Imperatives: Importance of CIS […]
In the landscape of cybersecurity and data protection, achieving compliance with regulatory standards is paramount. However, while compliance frameworks provide essential guidelines, they often overlook a crucial element: server hardening. This missing piece in the puzzle of continuous compliance plays a pivotal role in fortifying systems against evolving threats, complementing, and strengthening adherence to regulatory […]
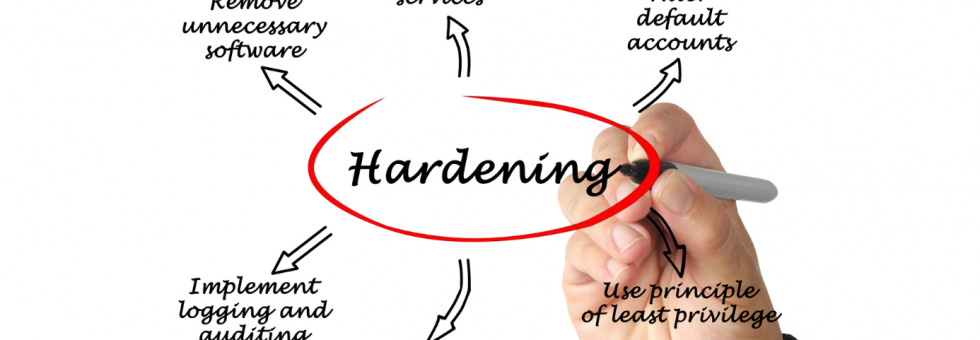
Server Hardening The server hardening process reduces your business’ attack surface and helps you guard against ransomware, malware, and other cyberthreats. You can follow this process to protect all points of entry against cyberattacks, address cybersecurity weaknesses, and optimize your security posture. What Is Server Hardening? A server is a computer program or device that […]
The Centre for Internet Security (CIS) benchmarks are a set of compliance best practices for a range of IT systems and products. These benchmarks provide the baseline configurations to ensure both CIS compliance and compliance with industry-agreed cybersecurity standards. While CIS Benchmarks are valuable, they’re also crucial to regulatory compliance. CIS compliance standards create frameworks […]
As technology evolves and industries become more regulated, businesses are increasingly required to comply with various regulations and standards. Continuous compliance, also known as ongoing compliance, is the ongoing process of meeting these regulatory requirements and maintaining compliance in all aspects of business operations. In this blog, we will explore the importance of continuous compliance […]
In the ever-evolving landscape of technology and data governance, compliance remains a pivotal aspect for organizations across industries. It serves as the bedrock for trust, security, and reliability, ensuring adherence to regulatory standards, internal policies, and industry best practices. However, traditional compliance approaches often presented challenges, especially in the face of dynamic infrastructures and rapidly […]
In the dynamic realm of cybersecurity, the stakes have never been higher. As threats continue to evolve, organizations are faced with the challenge of maintaining robust security postures while keeping pace with the latest standards. One solution stands out as a game-changer: the automation of CIS (Center for Internet Security) compliance. Let’s delve into the […]
In the ever-evolving landscape of cybersecurity, staying ahead of threats is not just a goal but a necessity. Meet AutomateCIS, your comprehensive solution for automating OS/application/cloud hardening based on CIS standards. AutomateCIS understand the critical importance of adhering to cybersecurity best practices, and its cutting-edge platform ensures not only compliance but a proactive defense strategy. […]
Compliance In the world of healthcare, safeguarding patient data isn’t just a priority—it’s a legal and ethical imperative. The Health Insurance Portability and Accountability Act (HIPAA) mandates stringent measures to protect Electronic Protected Health Information (ePHI), making compliance a non-negotiable aspect for healthcare organizations. Among the arsenal of security strategies, CIS (Center for Internet Security) […]
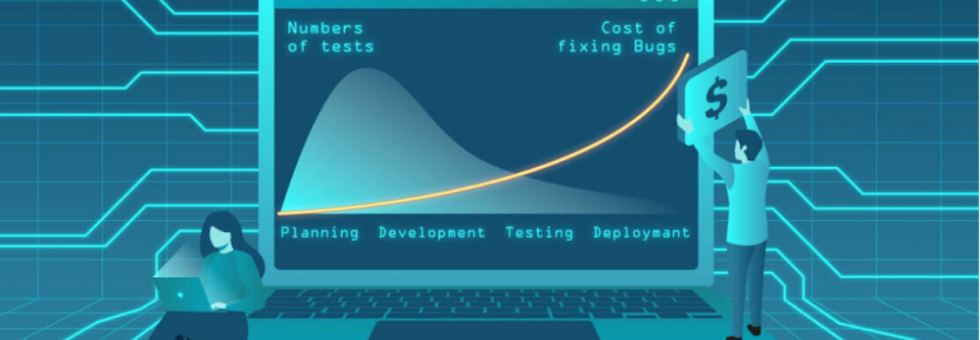
This article delves into the essential strategies and practices that enable organizations to adopt Shift Left Security seamlessly in their cloud environments. In an era where cloud computing reigns supreme, the concept of security has undergone a profound transformation. As businesses rapidly migrate their operations and data to the cloud, the need to secure this […]